Terraform is an open-source infrastructure as code (IaC) tool that is widely used in the field of DevOps. It allows users to define and provision infrastructure resources declaratively, making managing and scaling infrastructure easier. Terraform has gained popularity due to its simplicity, flexibility, and ability to work with multiple cloud providers.
Understanding the Basics of Terraform
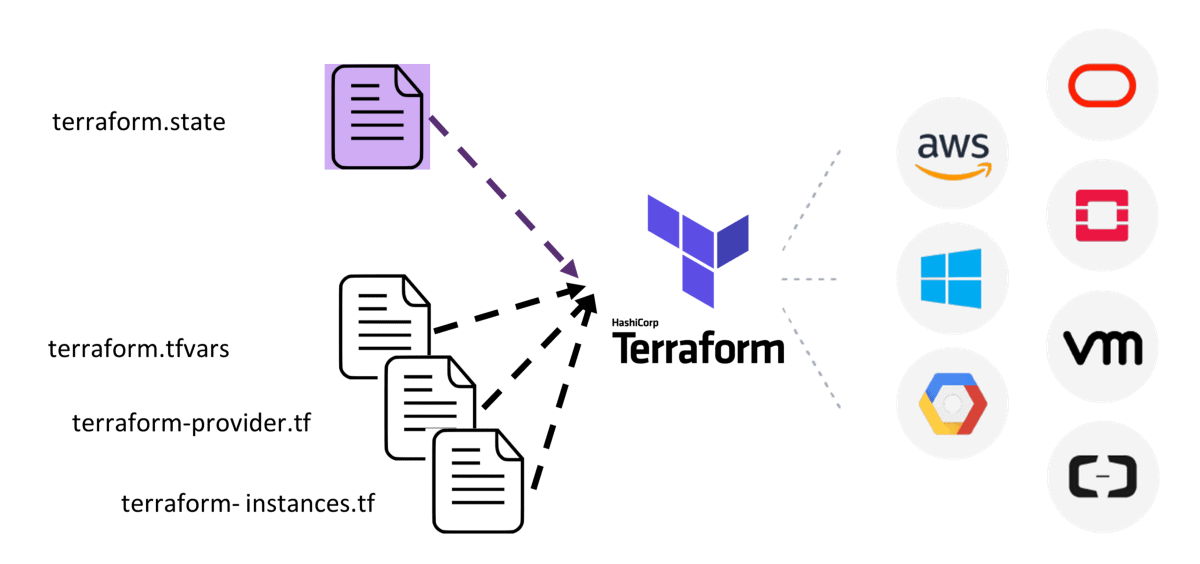
Terraform is a tool developed by HashiCorp that allows users to define and provision infrastructure resources using simple and declarative language. It uses a configuration file, written in HashiCorp Configuration Language (HCL), to describe the desired state of the infrastructure. Terraform then compares the desired shape with the current state and makes the necessary changes to bring the infrastructure into the desired shape.
One of the key features of Terraform is its ability to work with multiple cloud providers, such as AWS, Azure, and Google Cloud Platform. This allows users to manage their infrastructure resources across different cloud providers using a single tool. Terraform supports various resource types, including virtual machines, storage accounts, networks, and load balancers.
Terraform has distinct advantages over other infrastructures, such as code tools like Ansible and Chef. Firstly, Terraform is cloud-agnostic, meaning it can be used with any cloud provider that has a Terraform provider available. This allows users to choose the best cloud provider for their needs without learning a new tool. Secondly, Terraform uses a declarative language, which makes it easier to understand and maintain infrastructure code. Lastly, Terraform has strong community support and many modules, making it easier to get started and leverage existing code.
The Importance of Infrastructure as Code
Infrastructure as code (IaC) is an approach to managing infrastructure resources using machine-readable configuration files. It allows users to define and provision infrastructure resources consistently and repeatedly, reducing the risk of human error and increasing the efficiency of infrastructure management.
One of the key benefits of infrastructure as code is the ability to version control infrastructure configurations. This allows users to track changes to infrastructure code over time, roll back to previous versions if needed, and collaborate with other team members more effectively. Infrastructure as code also enables automation, as infrastructure configurations can be easily integrated into continuous integration and continuous deployment (CI/CD) pipelines.
Terraform plays a crucial role in enabling infrastructure as code. Its declarative language and support for multiple cloud providers make it a powerful tool for managing infrastructure resources. With Terraform, users can define their infrastructure configurations in a single file, which can then be version-controlled, shared, and reused across different environments.
Common Terraform Use Cases in DevOps
Terraform is widely used in DevOps for various use cases. One common use case is provisioning and managing cloud infrastructure resources. With Terraform, users can define their desired infrastructure state in a configuration file and then use Terraform commands to create, update, or destroy the resources. This makes it easier to manage infrastructure resources across different environments and cloud providers.
Another common use case is creating and managing Kubernetes clusters. Terraform has built-in support for provisioning Kubernetes clusters on popular cloud providers such as AWS, Azure, and Google Cloud Platform. Users can define their desired Kubernetes cluster configuration in a Terraform module and then use Terraform commands to provision the cluster.
Terraform is also used for managing network infrastructure, such as virtual networks, subnets, and security groups. With Terraform, users can define their network configuration declaratively and then use Terraform commands to create or update the network resources. This makes managing complex network configurations easier and ensures consistency across different environments.
Best Practices for Terraform Configuration Management
When working with Terraform, following best configuration management practices is important to ensure the infrastructure code’s reliability and maintainability. Here are some tips for organizing and writing Terraform code:
1. Organize Terraform code into modules: Modules are reusable units of Terraform code that can be used to provision infrastructure resources. Organizing Terraform code into modules can promote reusability, reduce duplication, and make the code more maintainable.
2. Use variables and outputs: Variables allow you to parameterize your Terraform code, making it more flexible and reusable. Results will enable you to expose certain values from your Terraform code, making it easier to consume in other parts of your infrastructure.
3. Use version control: Version control is essential for managing infrastructure code. Use a version control system, such as Git, to track changes to your Terraform code over time, collaborate with other team members, and roll back to previous versions if needed.
4. Use a consistent naming convention for your resources to make understanding and managing your infrastructure easier. This includes naming conventions for resource types, resource names, and resource tags.
5. Use modules from the Terraform Registry: The Terraform Registry is a repository of pre-built modules that can be used to provision infrastructure resources. Using modules from the registry can save you time and effort, as you can leverage existing code instead of writing everything from scratch.
Terraform Modules and Reusability
Terraform modules are reusable units of Terraform code that can be used to provision infrastructure resources. Modules allow you to encapsulate a set of resources and their configurations into a single unit, which can then be reused across different environments or projects.
There are several benefits of using Terraform modules. Firstly, modules promote reusability by allowing you to define infrastructure resources once and then reuse them across different environments or projects. This can save you time and effort; you don’t have to write the same code multiple times. Secondly, modules make your infrastructure code more maintainable by encapsulating resources and their configurations into a single unit. This makes understanding, updating, and troubleshooting your infrastructure code easier. Lastly, modules can be shared with the community through the Terraform Registry, allowing others to benefit from your code and contribute to its improvement.
To create a Terraform module, you must define a set of resources and their configurations in a separate directory. The module directory should contain a main.tf file that defines the resources, a variables.tf file that defines the input variables for the module, and an outputs.tf file that defines the output values of the module. Once you have created a module, you can use it in other parts of your infrastructure code by referencing its source location.
Managing State in Terraform
Terraform state is a key concept in Terraform that represents the current state of your infrastructure. Terraform uses it to track changes to your infrastructure over time and determine what actions must be taken to bring it into the desired state.
Managing Terraform state is important for several reasons. Firstly, the Terraform state contains sensitive information, such as resource IDs and access keys, which should be protected from unauthorized access. Secondly, the Terraform state is used by Terraform to determine what actions need to be taken to bring the infrastructure into the desired shape. If the condition is not managed properly, it can lead to inconsistencies and errors in your infrastructure.
There are several best practices for managing Terraform state. Firstly, store your Terraform state in a remote backend, such as AWS S3 or Azure Blob Storage. Keeping the state remote ensures it is accessible from anywhere and can be easily shared with other team members. Secondly, enable versioning for your Terraform state. Versioning allows you to track changes to your state over time, roll back to previous versions if needed, and collaborate with other team members more effectively. Lastly, encrypt your Terraform state to protect sensitive information. Most remote backends support encryption at rest, ensuring your condition is protected from unauthorized access.
Working with Cloud Providers in Terraform
Terraform provides a unified interface for working with cloud providers like AWS, Azure, and Google Cloud Platform. This allows users to manage their infrastructure resources across other cloud providers using a single tool.
You must configure a provider block in your Terraform code to work with a specific cloud provider in Terraform. The provider block specifies the credentials and settings required to authenticate with the cloud provider and interact with its AP.
Once the provider block is configured, you can use Terraform commands to create, update, or destroy resources on the cloud provider.
When working with different cloud providers in Terraform, it is important to follow best practices to ensure consistency and reliability. First, use the same naming conventions and resource configurations across different cloud providers to make managing and understanding your infrastructure code easier. Secondly, use the appropriate resource types and designs for each cloud provider. Each cloud provider has its resource types and designs, so use the ones specific to the one you are working with. Lastly, test your infrastructure code on a staging or development environment before deploying it to production. This lets you catch any issues or inconsistencies before they affect your production environment.
Terraform Integration with CI/CD Tools
Continuous integration and continuous deployment (CI/CD) is an approach to software development that involves automating the process of building, testing, and deploying software changes. CI/CD tools allow users to automate various tasks, such as code compilation, unit testing, and infrastructure provisioning, to ensure that software changes are delivered quickly and reliably.
Terraform can be integrated with CI/CD tools to automate the process of provisioning and managing infrastructure resources. This allows users to include infrastructure changes as part of their CI/CD pipelines, ensuring that infrastructure is provisioned and updated consistently and repeatedly.
To integrate Terraform with CI/CD tools, you must configure your CI/CD pipeline to execute Terraform commands as part of the deployment process. This can be done using a script or a plugin provided by the CI/CD tool. The Terraform commands can create, update, or destroy infrastructure resources based on the changes in your infrastructure code.
When integrating Terraform with CI/CD tools, it is important to follow best practices to ensure the reliability and security of your infrastructure. Firstly, use separate environments for different stages of your CI/CD pipeline, such as development, staging, and production. This allows you to test your infrastructure changes in a controlled environment before deploying them to show. Secondly, use version control for your infrastructure code and include it in your CI/CD pipeline. This ensures that changes to your infrastructure code are tracked, tested, and deployed in a controlled manner.
Troubleshooting Common Terraform Issues
Like any other tool, Terraform can sometimes encounter issues that must be resolved. Here are some common problems that arise when using Terraform and how to troubleshoot them:
1. Dependency errors: Dependency errors occur when there are circular dependencies between resources in your Terraform code. To resolve this issue, you can use the depends_on argument to define how resources should be created or updated explicitly.
2. State lock errors: State lock errors occur when multiple users or processes try to modify the same Terraform state simultaneously. To resolve this issue, you can use a remote backend that supports state locking, such as AWS S3 or Azure Blob Storage. State locking ensures that only one user or process can modify the state at a time, preventing conflicts and inconsistencies.
3. Provider errors: Provider errors occur when there are issues with the configuration or authentication of the cloud provider in your Terraform code. To resolve this issue, double-check your provider configuration and credentials to ensure they are correct. You can also check the provider documentation for known issues or troubleshooting steps.
4. Resource conflicts: Resource conflicts occur when there are conflicts between the desired state and the current state of your infrastructure. To resolve this issue, you can use Terraform commands such as terraform plan and terraform apply to compare the desired shape with the current state and make the necessary changes.
To avoid common Terraform issues, following best practices for configuration management and stent and working with cloud providers are important. This includes organizing your Terraform code into modules, using version control for your infrastructure code, managing Terraform state properly, and following best practices for working with different cloud providers.
If you are preparing for a DevOps interview that includes questions about Terraform, here are some common Terraform-related interview questions and tips for preparing:
1. What is Terraform and how does it work?
– Prepare a brief overview of Terraform and its key features.
– Understand how Terraform uses declarative language to define infrastructure resources and compares the desired state with the current state to make changes.
2. What are the benefits of using Terraform in DevOps?
– Prepare a list of benefits, such as infrastructure, code, automation, and support for multiple cloud providers.
– Provide examples of how Terraform can improve efficiency, scalability, and reliability in infrastructure management.
3. How do you manage Terraform state?
– Explain the importance of managing Terraform state and the risks of not managing it properly.
– Describe best practices for managing Terraform state, such as storing it in a remote backend, enabling versioning, and encrypting.
4. How do you work with different cloud providers in Terraform?
– Explain how Terraform provides a unified interface for working with different cloud providers.
– Describe how to configure a provider block in your Terraform code and use Terraform commands to create, update, or destroy resources on the cloud provider.
5. How do you integrate Terraform with CI/CD tools?
– Explain the concept of CI/CD and its benefits in software development.
– Describe how Terraform can be integrated with CI/CD tools to automate infrastructure provisioning and management.
To prepare for these questions, review the Terraform documentation, practice writing Terraform code, and familiarize yourself with common use cases and best practices.
Terraform is a powerful tool that plays a crucial role in DevOps by enabling infrastructure as code and automating infrastructure provisioning and management. By understanding the basics of Terraform, the importance of infrastructure as code, common use cases in DevOps, best practices for configuration management, and how to work with different cloud providers and integrate with CI/CD tools, you can leverage Terraform to improve efficiency, scalability, and reliability in your infrastructure management. By following best practices and preparing for Terraform-related interview questions, you can enhance your skills and advance your career in DevOps.







