A lately-discovered macOS malware referred to as OSX Dok, which alters the working device to subvert the safety measures put in the area, has now commenced mirroring banking websites in keeping with researchers trying to steal sensitive records from machines which might be inflamed by using it.
The malware, which makes use of ‘phishing’ and ‘man within the center’ assaults to sneak onto an unsuspecting user’s laptop, turned into located back in May using ESET. Initially, it only tricked people into allowing get admission to their key chain; however, due to the fact then, it has morphed and is now focused on their financial institution accounts. As Checkpoint explains:
“They are aiming at the sufferer’s banking credentials through mimicking essential financial institution sites. The faux websites activate the patient to install software on their cellular devices, that can potentially lead to also infection and records leakage from the mobile platform as properly.”
Apple, however, has endured revoking the certificate that the malware used to advantage get right of entry to the underlying system, but this appears to have had little to no effect on it up to now. Researchers stated that the organization at the back of the worm has persisted in getting new certificates, which they defined as a ‘surge in activity with new compromised certifications being purchased each day.
As it is frequently recognized, phishing tends to mimic a relied-on supply, inclusive of a password reset electronic mail despatched by Apple or your bank. These redirect customers to compromised websites where the victim is asked to go into their details, which are then used to get admission to your data or money owed.
Although organizations like Google, Microsoft, and Apple have endured the combat in opposition to these attacks, Brad Smith from Microsoft calling for a ‘Digital Geneva Convention.’ It is up to the person to make certain that the best click on hyperlinks from dependent on assets. Many commercial establishments replace their respective websites with warnings about new threats, and it’s miles usually recommended maintaining your self-updated with what is going on, mainly with the recent increase in cyber-assaults. You can also study up on these telltale signs of spotting suspicious electronic mail.
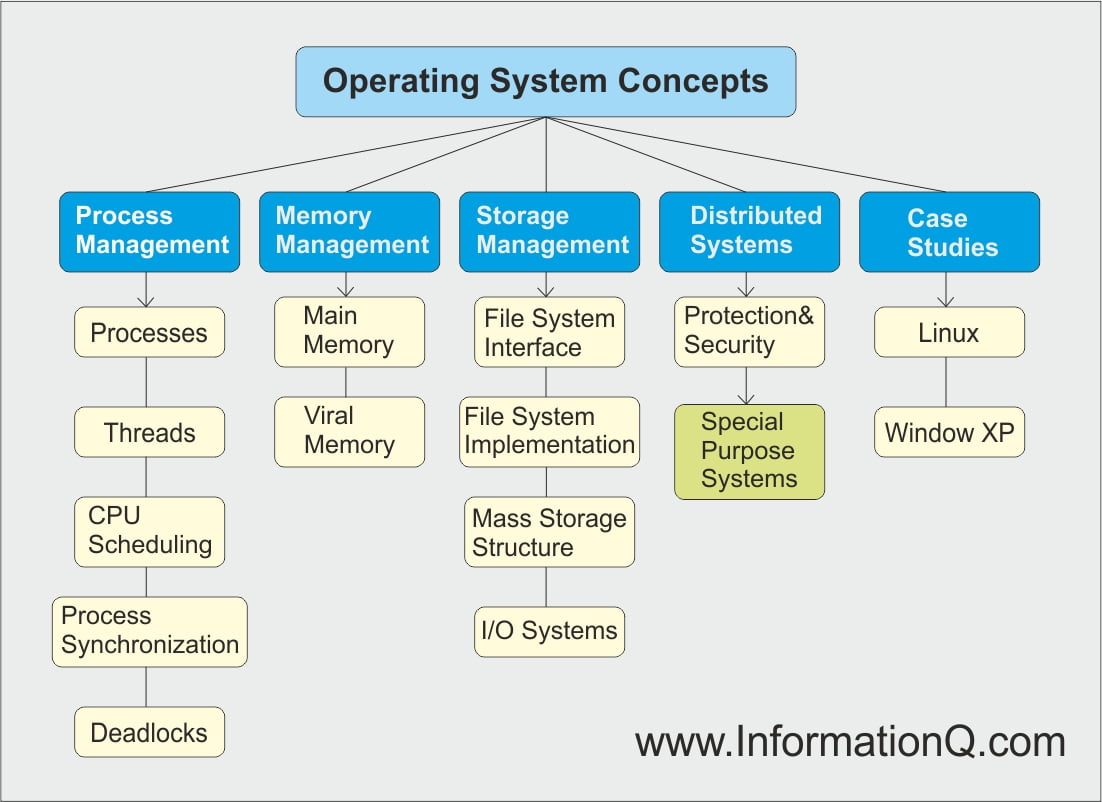
How Secure Is Your Operating System?
Ever wonder how comfy your information is? What protection protocols do you practice? Maybe creating a password? Locking the pc so others cannot access your statistics? Bypassing home windows passwords best takes a minute or less, and the home windows ten installation disk. Thus a long way, I had managed to use the Windows 10 disk to pass account passwords and even activated deactivated accounts on Windows Server 2012, Windows 10, Windows 7, and Windows eight.1. I have not begun to test the method to bypass locked computer accounts in Windows XP and Vista. However, I do now not foresee any complications with the ones operating systems.
Before you observed, this makes you safer because you operate Mac OS X. I even have also been capable of skip root level account passwords on a MacBook Pro, walking Mac OS X (10.10) Yosemite working gadget, the use built-in Apple commands. This approach also took less than a minute to perform.
The protection carried out in a running machine and accounted consistently has a stage of vulnerability. Most safety features are felt proper techniques. Username and passwords, for example, represent single-level authentication, identifying who you’re, the username and evidence that you are who you’re, the password. It is said that modern-day safety protocols require the username to be specific and the password to have no less than sixteen characters, and a random combination of uppercase, lowercase, numbers, and unique characters to be applied. Sixteen digits the quantity of the average person to remember their very own passwords. With the developing technological advancements of laptop processing energy, such passwords will subsequently be able to be broken in shorter amounts of time, in the end making them utterly vain. Most running systems save username and password mixtures as hash algorithms in particular documents that can be considered plain textual content, ensuring the need for passwords to be obsolete.
Stating one’s information no longer means “So, why trouble?” with username and passwords. Passwords do forestall the familiar character from gaining admission, and some degree of security is better than no degree of safety. There, of the route, are different ways to higher comfy your operating structures, stopping the method stated here from being applied. Data at rest encryption, for example, is a choice at the working gadget degree. In this manner, a decryption method needs to occur previous to the running device boot.
Two aspects and 3-component authentication also boom the security degree of your working device. CAC (Common Access Cac) playing cards, generally used by the DoD and other government groups, are a top example of two-component authentication. The first aspect, requiring the card itself that maintains an encrypted certificate to pick out who you’re and who you assert you’re, plus the second element of a pin as secondary proof. 3-component authentication would encompass functions inclusive of biometrics. Keep in thoughts, despite all of those techniques being utilized. There isn’t any such element as a 100% secure machine.
The Holy Spirit Or Ego – Which Is Your Operating System?
You are probably discouraged, thinking that gaining knowledge of overlooking the ego takes time, and the effects you may wish for from the Holy Spirit are too far into the destiny; you may want to surrender. This impatient-kind questioning is what the ego desires. Instead, try to view this in a more right-minded fashion.
The Holy Spirit makes use of time in His very own way, based totally on your wishes, your stage of readiness, and your potential to shift over to right-minded perception. Remember, the Holy Spirit will use ego devices and ego-based minds while He unearths them beneficial to your gain.
Any waste of time you feel is your identification with the ego, which uses time for destruction. The ego will use a chance to convince you that there isn’t always enough of it and that anything you enjoy will come to a stop.






